SSH - Using Keys Instead of Passwords
Last updated: Mar 26, 2008SSH is really not that secure by default on must Linux distributions in the default configuration. By default OpenSSH is configured to allow password based authentication (because its easier); however, script kiddies have developed scripts that can try thousands of passwords an hour. If you have a strong secure password this will usually not be an issue but if you or one of your users use a dictionary based or weak password your system can be compromised quite easily. Most of the time you have no control over the strength of your users passwords so I recommend giving them a password that is 1024 bits, also known as a private key. Since this key is stored in a text file on the users machine it is often times a good alternative way of authenticating for users that don’t want to remember passwords but still be very secure.
 Since the 1024 bit private key must match the public key we have 21024 or 1.797693134 x10308 keys. That is a 1 with 308 zeros behind it. If you were to process 1 billion passwords per second you would still not be able to crack this password within a few million years. Although this method is impervious to brute force attacks it is worthless if you leave your private key out for everyone to see, so after you get this setup guard it! It is worth mentioning that you can set a pass phrase on your private key. This way if your private key does fall into the wrong hands it will be worthless.
Since the 1024 bit private key must match the public key we have 21024 or 1.797693134 x10308 keys. That is a 1 with 308 zeros behind it. If you were to process 1 billion passwords per second you would still not be able to crack this password within a few million years. Although this method is impervious to brute force attacks it is worthless if you leave your private key out for everyone to see, so after you get this setup guard it! It is worth mentioning that you can set a pass phrase on your private key. This way if your private key does fall into the wrong hands it will be worthless.
Setting up SSH to Use DSA Keys
On the machine running sshd:
$ ssh-keygen -t dsa
it should give you something like this:
Generating public/private dsa key pair.
Enter file in which to save the key (/home/mark/.ssh/id_dsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/mark/.ssh/id_dsa.
Your public key has been saved in /home/mark/.ssh/id_dsa.pub.
The key fingerprint is:
bb:f6:0e:6d:b5:c5:5f:c3:a1:d6:73:5f:25:f9:4d:09 mark@beasd
Notice how it saved the private key as id_dsa and the public key as id_dsa.pub in the ~/.ssh directory.
Since most sshd configurations are set to look for public keys in ~/.ssh/authorized_keys we shall add our new public key to that file:
$ cat ~/.ssh/id_dsa.pub >> ~/.ssh/authorized_keys
After adding the newly generated public key to authorized_keys you should be able to authenticate with keys. Try it now on the localhost like so.
$ ssh localhost -i .ssh/id_dsa
The ‘-i’ flag tells ssh to identify with a key.
If your login was successful it should be safe to turn of keyboard/password authentication. Edit /etc/ssh/sshd_config
Make sure you have these set to yes to enable the use of keys:
RSAAuthentication yes
PubkeyAuthentication yes
After you have your key working you should turn of regular password authentication:
PasswordAuthentication no
ChallengeResponseAuthentication no
Might as well turn off root login for security purposes
PermitRootLogin no
Connecting From a Windows Computer Using PuTTY
The most common ssh client for Windows is PuTTY so I will explain how to connect to your newly configured ssh server with PuTTY. You will also need puttygen to convert the key to a key that putty can use (*.ppk files).
First start off by copying the id_dsa.pub from your ssh server to your machine with whatever method you want. I used FTP. Then open PuTTYgen.exe. If you set up a pass phrase you will be prompted to type it in.
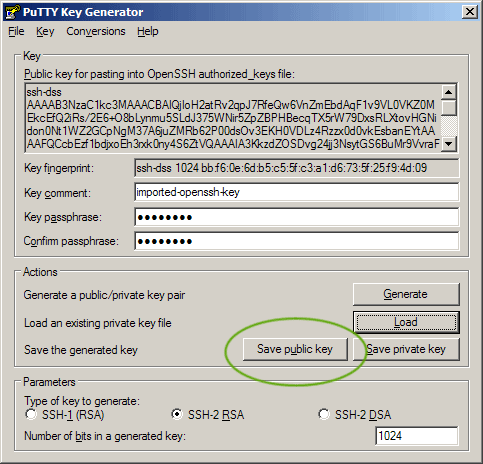
Click load to load a previous private key. Then save it as a .ppk.
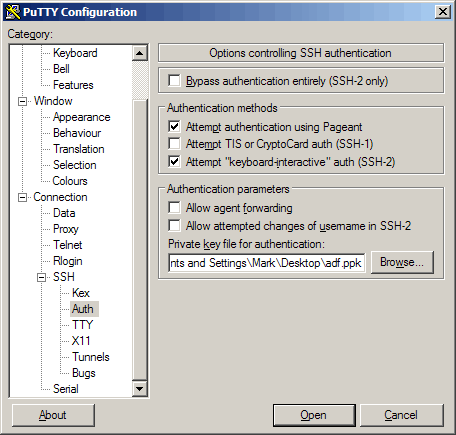
Then open PuTTY and enter the IP address of the SSH server and click on ssh > auth in the tree to the left:
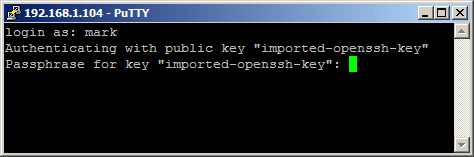
Click browse and find the .ppk file you just saved. Then hit open. If all goes well you should be greeted with something similar to this:
Need to print shipping labels on your site?
Checkout my product RocketShipIt for simple easy-to-use developer tools for UPS™ FedEx™ USPS™ and more.